![ConnectedCarSec [Converted]](https://jessgroopman.files.wordpress.com/2016/06/connectedcarsec-converted.png)
What once seemed far-fetched, niche, even space-age is now central to the immediate roadmap of just about every automotive manufacturer in the world.
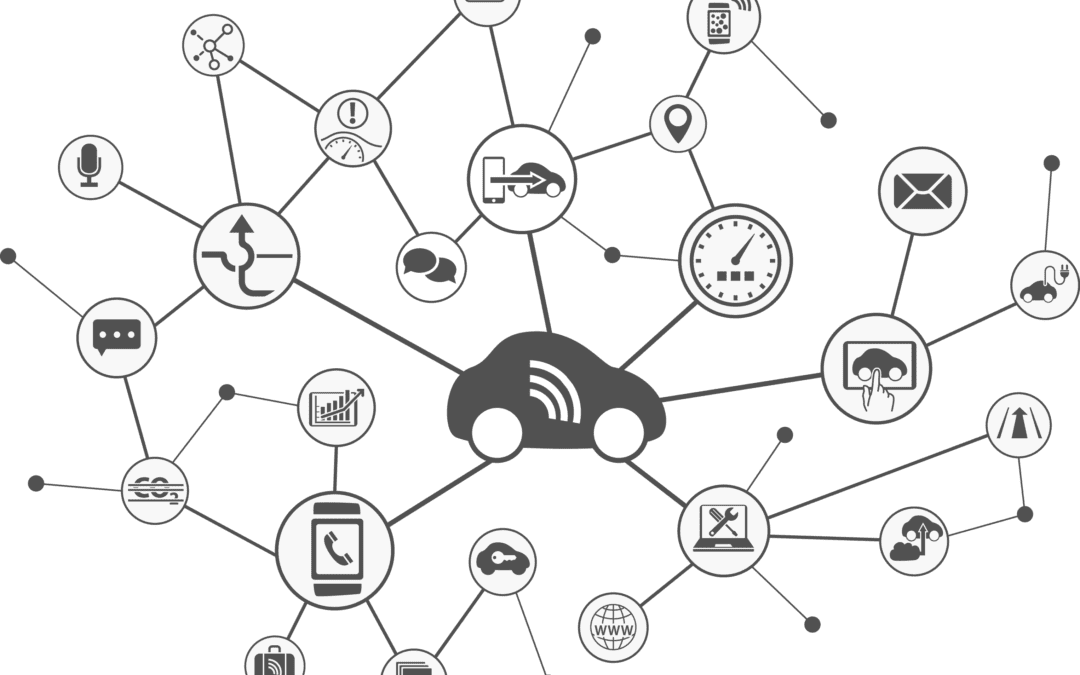
In reality, connected cars aren’t all that new: sensors, telemetry, even performance data have been part of automotive DNA for years. Yet suddenly, the very notion of the car—its function, the business model(s) that underpin it, notions of ownership, and the experience of driving as we have always known it— are transforming. However, as the technology of the car transforms from a ‘dumb’ frame of metal and mechanical parts to ‘smart’ hardware-software computing platform, the outcome isn’t just an increase in functions and services, but significant increases in vulnerability as well.
The infusion of networked services, sensors, and data in the objects and infrastructures around us simultaneously generate unpredicted value and risk. The rise of connected and eventually autonomous cars implies the rise of vehicle-based apps, which inherently represent the threat of car-hacking. Today there are an estimated 13.3 million connected cars on the road. Harbor Research forecasts a 33.7% compound annual growth rate in this market, skyrocketing to some 101.5 million connected cars by 2022. Meanwhile, “the average security level within these vehicles is equivalent to that of IT systems and computers from the ’80s, with limited encryption, data protection and identity management,” notes Simon Moffatt, director Advanced Customer Engineering at ForgeRock, a digital identity management platform.
Car-hacking can compromise three areas: Security, privacy, and most importantly, safety. In the emerging landscape of connected and autonomous driving, these three concepts are the central domain to understand as we adapt, adopt, and redefine our relationship with driving.
Cars are inherently risky. What’s different now?
Risk and cars go hand-in-hand. It doesn’t take connectivity to prove that. Already some 32,675 drivers die in motor vehicle-related accidents every year. But the risks inherent to a ‘smart’ cars are manifold because these vehicles are quickly becoming more like systems that single nodes. They are complex networks of data, sensors, mechanics, and users, transmitting information, acting in response to multiple stimuli, and connected across a variety of stakeholders. Thus to assess the vulnerability of a car requires we assess the vulnerability of the vehicle system as a whole.
A car is now a system with a broader and more diverse threat surface.
The security of a system is only as strong as its weakest point. A system inherently creates more value than a node, as well it engenders greater vulnerability due its wider threat surface. Within the system of any single car, consider the ecosystem of threats:
- Components of the Car (hardware & software): Control systems shut-down, application breach, application hijacking, user identity authentication, device identity authentication, authorization, physical intrusion, etc.
- Driver: Human error, exhaustion, intoxication, distraction, etc.
- Connectivity network(s): Cellular, wireless, satellite, fixed, low-power wide area, etc.
- Service providers: Insurance providers, advertising/media providers, mobile providers, in-car device manufacturers, financial service providers, etc.
- Outside forces: Cybercriminals, hackers, ransomware, cyber warfare
Moreover, threats across any system – a car in this case— don’t just have origins across a wide surface area, they are diverse in nature as well.
- Intrusion & penetration: Hacking, breaches, theft, cyber intrusion of in-vehicle devices, networks, value-added services, individuals, transportation mechanisms, infrastructure, etc.
- Manipulation of data: Nefarious use, manipulation, or exploitation of vehicle and/or driver data, device identity, assets, rules, features, services, system upgrades, compliance.
- Disruption of service: Disruption of functionality, features, security, services, functions, safety mechanisms, identity authentications, etc.
- Nefarious surveillance: Use of surveillance leveraged (by hackers, foreign states, terrorists, domestic law enforcement) for nefarious purposes, etc.
While security controls and infrastructure help protect privacy and safety, these concepts are distinct and generate their own sets of questions and considerations.
Privacy within the car is no longer a function of tinted windows. Connected cars inherently track drivers’ behaviors by tracking driving patterns. Acceleration, deceleration, location, and other vehicle control and movement data points are inextricably linked to individual drivers. Not only is our [every] interaction and behavior vis-à-vis the car empirical, it may also be cross-correlated or juxtaposed against other revealing data, sometimes data that can be reconstructed through multiple formulae. A driver leaving work, going to the bar with friends for one hour, stopping at a convenience store, may implicate or construct a narrative about that driver that goes beyond the basic data points of acceleration and deceleration, even without GPS tracking. How insurance companies (perhaps the same company covering car, home, motorcycle, etc.) will wield these data (and ensure their own security) beyond discounts remains unclear, especially to the public. As do privacy protections, mandates, and auditing mechanisms placed on data leveraged across industries and service providers. Many of the same questions and implications remain unclear for the second-hand car market as well.
Meanwhile, the public remains blissfully unaware of these risk and implications, never mind that such data will underpin emerging automotive business models…
Safety is at once the greatest risk and opportunity of connected cars. Since most accidents today occur as a result of human error, reducing human reliance and intervention logically renders autonomous driving a compelling notion. Technology lacks human discretion, the ability to imbibe, aggression, and countless other temptations and vulnerabilities unique, yet dangerous to the human [driving] experience. Given then, that even semi-autonomous connected cars are considerably less accident-prone, safety benefits of cars with advanced driver assistance systems (ADAS) span design and fuel efficiency, emergency response times, pedestrian environments, and so on. Even in the interim phase before fully autonomous vehicles, connected cars offer drivers safety improvements through software downloads enabling communication with other cars, navigation, self-parking, fuel conservation, and a host of other experiential enhancements. As cars grow even more sensor-aware, through vehicle-to-vehicle, vehicle-to-infrastructure, or other applications (V2X), other benefits emerge around increased safety for surroundings, infrastructure capacity, and traffic optimization.
But with in-vehicle software applications permeating the design and experience of connected cars, the threat of hacking, malware, cyberattack, or malfunction can compromise both cybersecurity and the physical safety of the car. Many examples exist already, perhaps most famously that of a hackers completely intercepting a Jeep Cherokee to the point of driving it off the road.
It’s time to accelerate innovation, not just in automotive features, but security and safety too
When we dismounted horses and stepped out of carriages, we never dreamed of the far-reaching benefits and simultaneous risks that we would confront in a world where cars and connected technology have both become ubiquitous. As we stand on the precipice of the next revolution in transportation, the industry must move toward developing better security controls and safeguards into and outside of the car. It must build ‘by design’ better identity mechanisms and integration controls, all while balancing a growing expectation for an altogether better driver experience. It must move towards strong partnerships and clear communications, roles, and protections for all stakeholders.
As technology evolves, so too will use cases, adopters, security threats, and cyber penetration techniques. All entities—OEMs, dealerships, service providers, government actors, even consumers—must recognize that security, and thus privacy and safety, in smart systems are not a binary “secure or insecure” achievement; rather security in the IoT is an ongoing cycle of assessment, re-evaluation, and optimization. Harbor Research offers a three-step framework to holistically address IoT security to aid in this quest. The impacts of connectivity in the automotive sector has the potential to transform virtually every part of the driving experience and value chain. And while such a road is ‘paved with good intentions,’ achieving this vision relies on our embracing a new approach to automotive security, privacy, and safety.